ARTICLE AD BOX
Report: Identity Has Become a Critical Security Perimeter for Cloud Services
- By David Ramel
- 05/07/25
A new threat landscape report points to new cloud vulnerabilities. According to the 2025 Global Threat Landscape Report from Fortinet, while misconfigured cloud storage buckets were once a prime vector for cybersecurity exploits, other cloud missteps are gaining focus.
"Cloud services now sit at the center of modern operations, and identity has become one of the most critical security perimeters," said a post exploring the report from the company's FortiGuard Labs. "Cloud breaches are no longer limited to misconfigured storage buckets. As infrastructure migrates to the cloud, attackers are finding familiar footholds to exploit, such as over-permissioned identities, credential leaks in public code repositories, and lateral movement through cloud-native services.
"FortiCNAPP telemetry shows that attackers often begin by logging in from unfamiliar geographies, sometimes within hours of a developer's legitimate activity. From there, they escalate privileges, establish persistence, and use legitimate services to blend into normal network traffic. In 2024, 25% of all cloud incidents began with reconnaissance, such as API enumeration, permission probing, and discovery of exposed assets."
That telemetry is key to the report, which is based on Fortinet's global sensor network and threat intelligence, and that intelligence suggests the advantage enjoyed by threat actors is growing, and will continue to do so until organizations change how they measure and manage risk.
One of the report's key findings, "Cloud attacks are evolving, but misconfigurations still reign," discusses the above finding in greater detail.
"Cloud environments remain a top target, with adversaries exploiting persistent weaknesses, such as open storage buckets, over-permissioned identities, and misconfigured services," the report said. "Lacework FortiCNAPP telemetry shows a steady rise in cloud compromises, often involving identity abuse, insecure APIs, and privilege escalation. These vectors are frequently combined in multi-stage attacks that leverage automation and legitimate services for stealth and persistence. Reconnaissance remains the most prevalent tactic, with attackers probing APIs, enumerating permissions, and scanning for exposed assets. In 70% of observed incidents, attackers gained access through logins from unfamiliar geographies, highlighting the critical role of identity monitoring in cloud defense."
The MITRE ATT&CK tactic distribution chart above shows some key takeaways of its own:
- Discovery (25.3%): The most common tactic in cloud attacks, indicating widespread scanning, enumeration of permissions, and probing of APIs and services.
- Initial Access (14.7%): Attackers most often gain entry through leaked or stolen credentials, phishing, or misconfigured authentication settings.
- Persistence (12.3%): Adversaries create or modify cloud identities and roles to maintain long-term access to compromised environments.
- Privilege Escalation (10.6%): Attackers manipulate permission policies or exploit cloud APIs to elevate their access rights.
- Impact (8.4%): Activities aimed at disrupting services, tampering with data, or initiating ransomware-like attacks in the cloud.
- Credential Access (7.9%): Techniques used to extract keys, passwords, or tokens for lateral movement or further exploitation.
- Lateral Movement (6.8%): Movement between cloud services, regions, or accounts after initial compromise, often undetected.
- Defense Evasion (6.1%): Methods used to avoid detection, such as using legitimate services or hiding malicious behavior in normal workflows.
- Collection (3.5%): Gathering sensitive data or metadata for later use or exfiltration.
- Exfiltration (3.3%): Stealing data from cloud storage, databases, or containers, often through abused APIs.
- Execution (1.2%): Running malicious scripts or binaries, typically through Bash, PowerShell, or Python in cloud workloads.
-

AWS, Microsoft, Google, Others Make DeepSeek-R1 AI Model Available on Their Platforms
Leading cloud service providers are now making the open source DeepSeek-R1 reasoning model available on their platforms, including Amazon, Microsoft, and Google.
-

2025 Cybersecurity Predictions for K-20 Education
What should K-12 and higher education institutions expect on the cybersecurity front in the coming year? Here's what the experts told us.
-

70% of Community College Students Are Working to Improve AI Career Readiness, Despite Mixed Feelings About AI
A recent report from IT training and certification provider CompTIA reveals the value of digital skills for community college students working toward career success.
-

Report: Enterprises Embracing Agentic AI
According to research by SnapLogic, 50% of enterprises are already deploying AI agents, and another 32% plan to do so within the next 12 months..
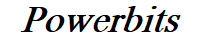





 English (US) ·
English (US) ·